Microsoft 365: Improving AMF Efficiency
Adding number matching and additional contexts to the Microsoft Authenticator app
I’m a big fan of using multi-factor authentication (MFA) to protect Azure AD accounts. At the risk of sounding like a broken record, Basic Authentication is a terrible thing to use for cloud accounts. Password brute-force attacks can steal user credentials and lead to tenant compromise. Microsoft is doing its best to remove Basic Authentication for Exchange Online. Tenants will have an incentive to better protect user accounts.
Another part of the puzzle is improving how MFA works to make it easier and more secure. Microsoft is revealing two new features for the Microsoft Authenticator app . I think all Microsoft 365 tenants should consider enabling number matching as soon as possible. Thirty minutes of admin work will improve user security (including the time to read the instructions). This isn’t always the case.
Two new features
Number matching means that during an MFA test, the user must enter a displayed number into Ms Authenticator to authenticate. This mechanism is already used for passwordless authentication.
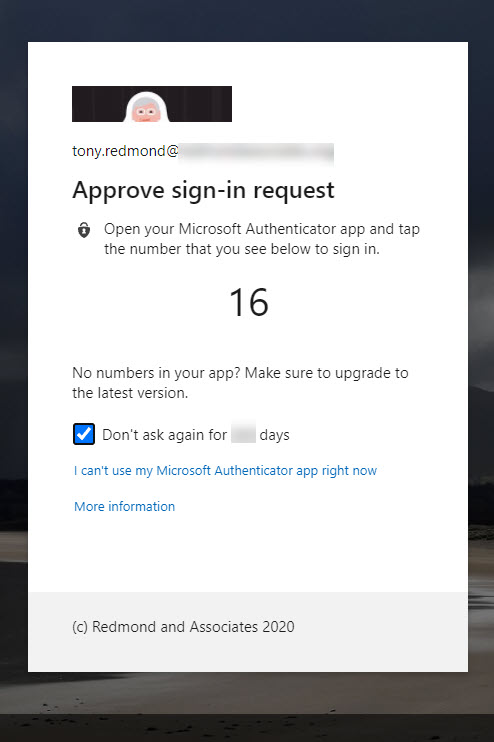
Additional context means the Authenticator app displays additional information to users when they need to approve an authentication request. Two pieces of information appear: the same information from the app requesting authentication and its login location based on the device’s IP address. Of course, the accuracy of a device’s IP address depends on many factors, and in some cases, it’s simply wrong. However, it’s enough to reassure people that the login attempt isn’t coming from an impossible location. And when combined with the number matching, it gives the user enough information to understand a more complete context of the authentication request.
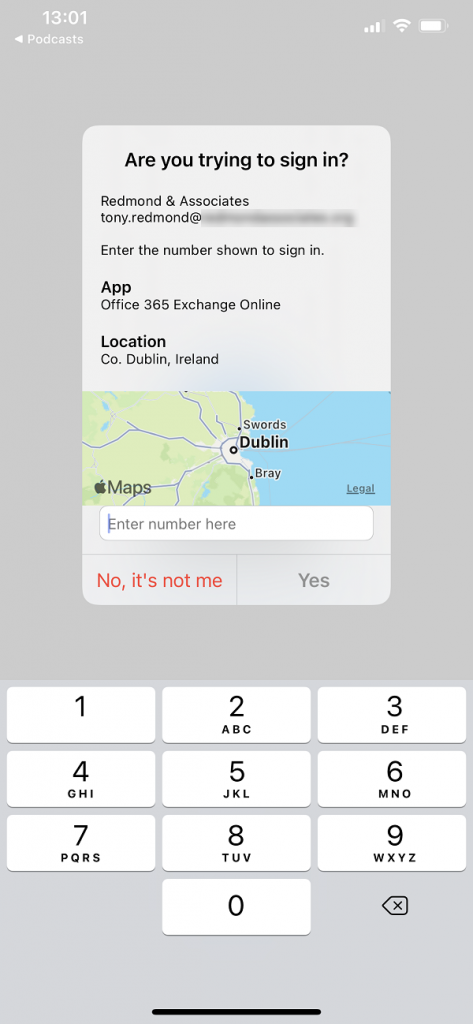
Update additional context and number matching via Azure AD admin center
You can enable additional context and number matching for Authenticator. To do this, update the settings in the Azure AD admin center. Go to the Authentication methods setting, select Microsoft Authenticator, and then click the […] option on the far right under the target to reveal the Configure flyout. Set the value for the Show additional context in notifications option and the value for the Enabled option.
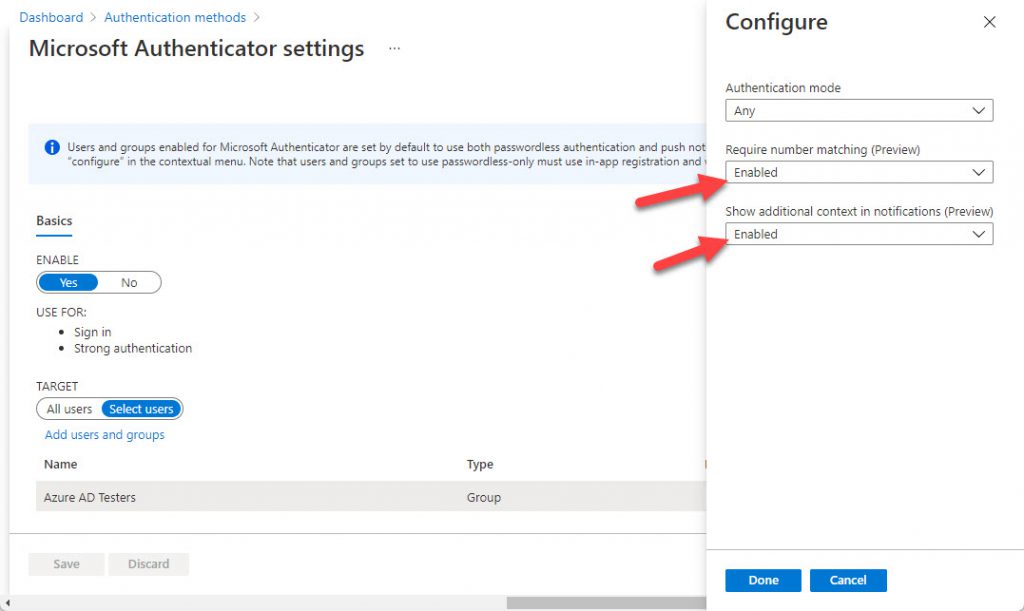
Both features are labeled “preview.” It is likely that they will become generally available in the near future.
Updating Authenticator configuration with Microsoft Graph Explorer
The easiest way to configure both features is to use the Azure AD admin center. You can also use the graph explorer to correct the Authenticator configuration.
Microsoft Graph Explorer
Microsoft Graph Explorer is a tool that every Microsoft 365 tenant administrator should be familiar with for running queries. Especially since the Graph APIs underpin many parts of Microsoft 365, some parameters and data are only accessible through Graph queries. You can still run commands through Graph Explorer. This way, you’ll see how queries work and what they return. You can also occasionally update tenant parameters. While there’s a GUI option in this case, this is a good example of using the Graph Explorer.
Enable number matching in Authenticator
To enable number matching for Microsoft Authenticator via Graph, follow these steps.
- Open Graph Explorer and log in with a tenant administrator account.
- Enter this query into the command box. Make sure you’ve chosen the beta endpoint (the default is V1.0), and then click Run Query.
https://graph.microsoft.com/beta/authenticationMethodsPolicy/authenticationMethodConfigurations/MicrosoftAuthenticatorChanging permissions
- You’ll likely get an error: Graph Explorer does not have the necessary permissions to access the Authenticator configuration. Click Edit Permissions, then click the Open Permissions Panel link to select Policy.ReadWrite.AuthenticationMethod from the Graph permissions set. Click Consent, and you’ll see the normal Permissions Requested dialog box to grant consent to the application. Accept the consent request and return to Graph Explorer.
- Run the query again. This time, Graph Explorer has the necessary permissions and the current configuration is displayed in the response box.
- Copy the JSON-formatted output and paste it into the request body above. Change the value of the numberMatchingRequiredState (number matching) and displayAppInformationRequiredState (additional context) properties to Enabled. Change only the values. Do not change the formatting or structure of the request body.
- By default, Graph Explorer runs GET requests to return information. If you want to update the settings, select PATCH from the query type drop-down list. The information displayed by Graph Explorer should look similar to Figure 4. Click Run query to make the change. If you see a “No content – 204” response, the change is effective. You can verify that the configuration settings match your expectations by changing the request type to GET and running the query to see the current configuration.
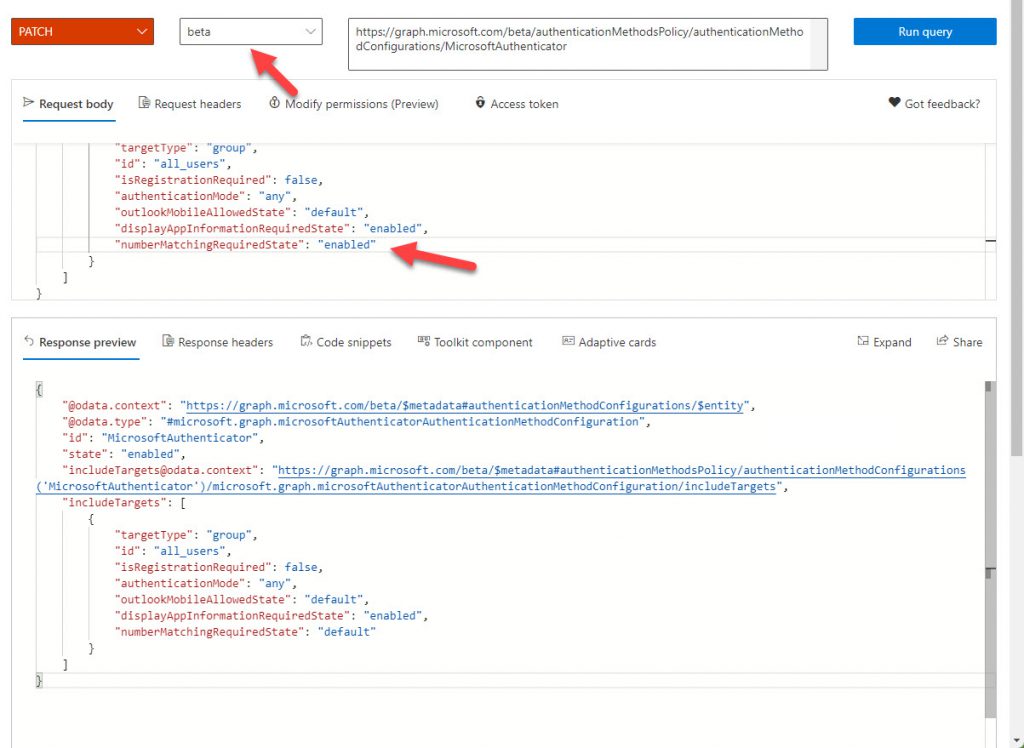
Of course, you can also check the Authenticator configuration in the Azure AD admin center.
Limit features to a specific group
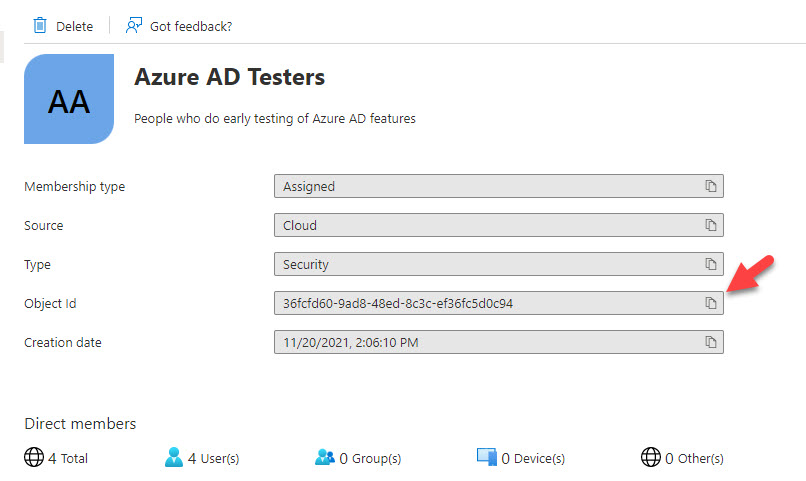
The approach described above enables number matching for all tenant members. You can also limit the functionality to a designated group by changing the Id property from “all_users” to the object ID of an Azure AD group. For example, suppose you have a group called Azure AD Testers. So, to get the group ID, search for it in the Azure AD admin center and copy the ID from the group properties (Figure 5).
You can also run this PowerShell command after connecting to the Azure AD endpoint:
Get-AzureADGroup -SearchString “Azure AD Testers”
ObjectId DisplayName Description
-------- ----------- -----------
36fcfd60-9ad8-48ed-8c3c-ef36fc5d0c94 Azure AD Testers People who do early testing of Azure AD featuresUpdate the Id property with the group ID (36fcfd60-9ad8-48ed-8c3c-ef36fc5d0c94 in our example) and run the PATCH request to limit feature access to members of the designated group. Also, don’t forget to run the GET request afterward to verify that the configuration contains the expected values.
Personally, I consider number matching and additional context to be so valuable that these features should be available to all users. However, I recognize that in tenant companies, it’s likely necessary to test and document any new feature before rolling it out broadly, so it’s good to have this flexibility.
The AMF continues on its way
Ultimately, Microsoft is steadily improving the usability of multi-factor authentication. Having a strong authenticator app is an important part of that work. Given this, it’s strange that so few tenants are using MFA to protect users. MFA is an important element in preventing attackers from breaking into Microsoft 365 tenants. Let’s hope this trend continues.

