Spam Filtering with Exchange Online Email Flow Rules
Définition
Mail flow rules are one of the layers of Exchange online protection processing. You may know them by their old name in Exchange Server, which was transport rules.
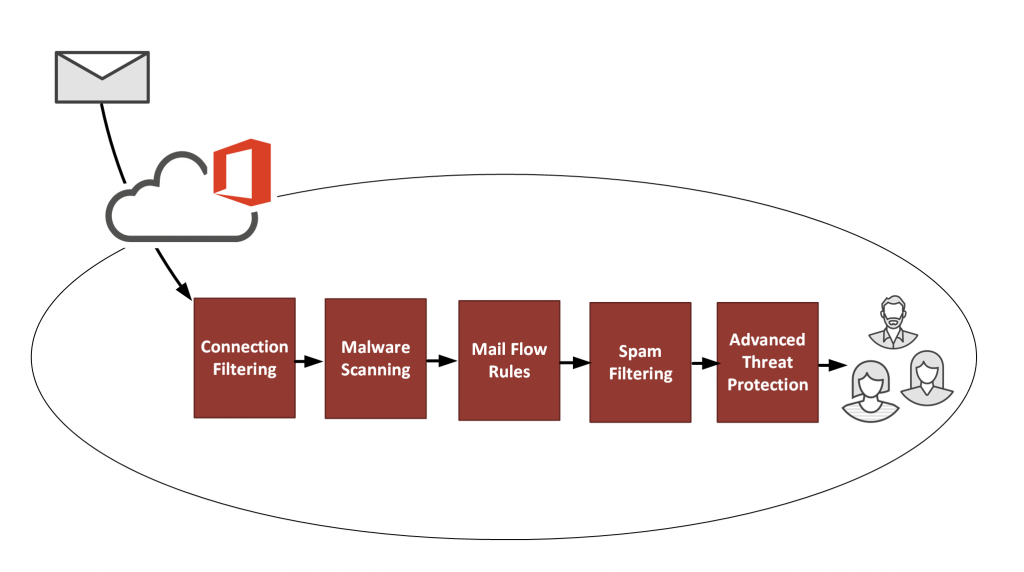
The name of transport rules used to align with the name of the Hub Transport server role , starting with Exchange 2007. In recent versions of Exchange, this role no longer exists. The Mailbox server role now provides this functionality. Transport rules and mail flow rules are the same thing. The capabilities of rules have improved a lot since the early days of Exchange 2007. And calling them mail flow rules makes more sense to some people. Because “mail flow” is an easy concept to understand. The name “transport” is a bit vague and wouldn’t make sense without understanding older versions of Exchange.
Mail flow rules can provide a wide range of policy enforcement results. They can also combat spam and other types of unwanted email.
Is it necessary to fight spam by creating mail flow rules in Exchange Online? Doesn’t that seem a bit old-fashioned to you? Especially when there are complex anti-spam algorithms working behind the scenes to protect Exchange Online?
The challenge
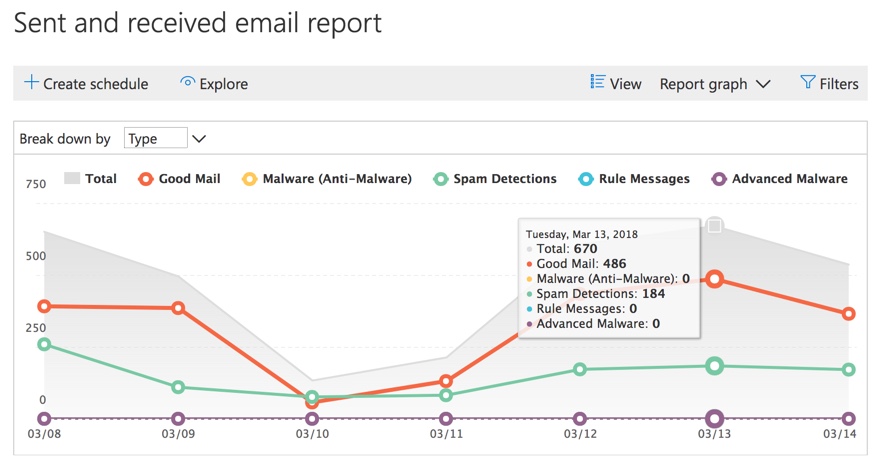
This is a valid question. It goes back to the good old days, when a lot of spam was blocked by very simple keyword rules. This was before anti-spam products evolved to include smarter detection. But even the smartest spam filters still miss things. And we need to use all the tools at our disposal to tailor our spam protection to our organization.
Sometimes this means creating mail flow rules to do things like:
- Allow or block specific IP addresses, domain names, and email addresses.
- Block specific keywords, whether it’s detecting text within the message or even a URL that the message might contain.
- Flag all incoming emails from external senders containing suspicious keywords.
Mail flow rules are also effective against new attacks and campaigns. Sometimes you need a quick solution while you wait for EOP to start detecting a new attack.
Yes, EOP should help you avoid most attack scenarios. But security is about mitigating risk using all reasonable means at our disposal.
Mail flow rules to bypass EOP
Here’s an example. Consider a sales contact form running on a company’s website. The company’s website is hosted on a shared hosting server provided by a web hosting company. The sales team wants to ensure that no emails from the contact form are filtered by Exchange Online Protection. Weakening the organization’s entire protection isn’t a good solution. Instead, one option to achieve this is to add the web server’s IP address to the list of allowed IPs in your EOP connection filter policy. This will prevent the connection filter from blocking the email.
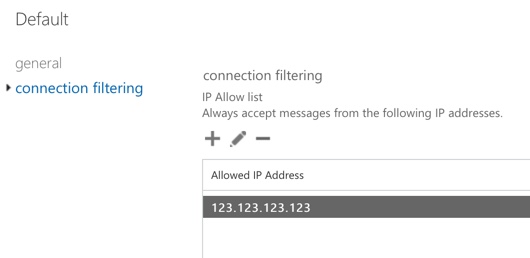
However, by using the allowed IP list, you allow all emails from that web server’s IP address to bypass your spam filters. In effect, you’re trusting the web hosting company to prevent other clients also on the shared hosting server from spamming or phishing your users. It’s unlikely the web hosting company will be able to prevent this. Furthermore, any insecurity in the web form itself could lead to abuse.
So, to strengthen your protection without exposing yourself to a new risk, you can use a mail flow rule instead. The mail flow rule is configured so that mail from the web server is still subject to spam filtering if it doesn’t have the specific characteristics of sales contact form emails. To do this, create a mail flow rule like the following:
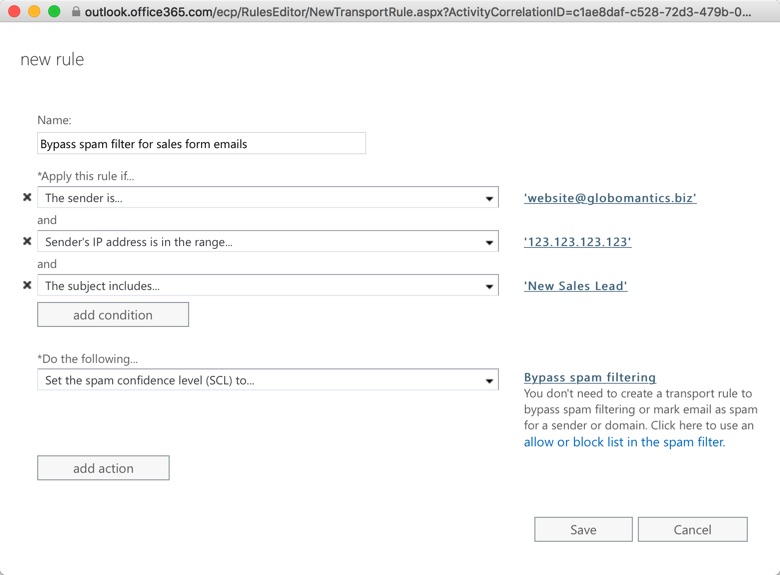
Mail flow rules against spam
Les règles de flux de courrier peuvent également être utilisées pour lutter contre les courriers Mail flow rules can also be used to combat malicious emails. Many phishing attacks rely on impersonating popular services like Amazon, Dropbox, DocuSign, and banks. These attacks can be difficult to detect, so they can slip through Exchange Online Protection’s defenses.
However, you can mitigate these risks by using mail flow rules. For example, with regex filters to detect likely phishing attempts. You can then either quarantine them or:
- send to spam folders,
- modify in some way to alert the user that the mail is suspicious.
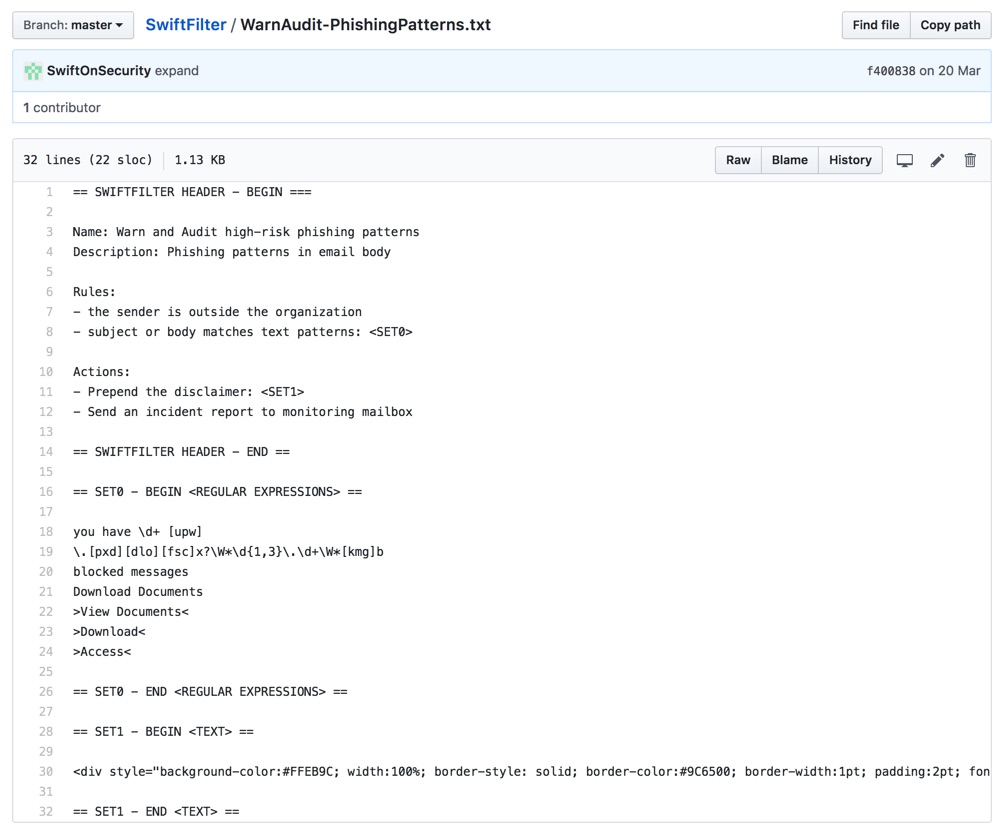
SwiftOnSecurity has helpfully shared a series of regex patterns and other text strings in this GitHub repository.
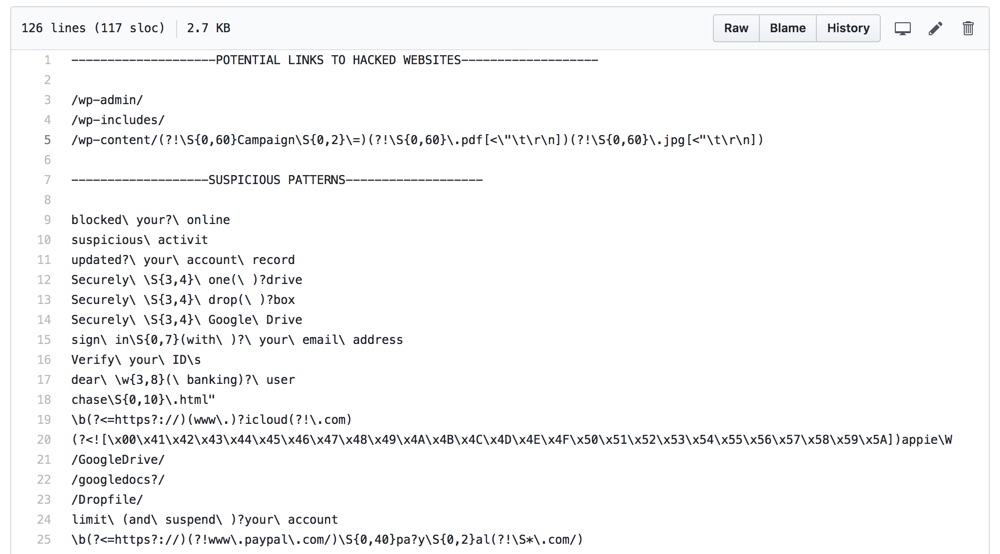
You should be careful when applying these patterns in your mail flow rules. I don’t recommend setting rules to immediately block mail before understanding what the filter catches. Using non-destructive actions, such as adding a preamble to the subject line, are reasonable approaches. Another good approach is to configure the rules to send incident notifications. Or, add a BCC recipient for a shared mailbox so you can review messages that trigger the rule. SwiftOnSecurity has another repository with details on mail flow rules that you can also use.
Summary
Exchange Online protection is an effective solution for preventing spam and phishing from reaching your users. However, we can do more to protect our organizations. Exchange Online mail flow rules offer a lot of flexibility to detect and mitigate specific risks. You can start with a few basic rules. Then expand them as you learn more about the threats specific to your organization.
Microsoft Defender: Getting the Most Out of Office 365 Policies

