Perform passwordless authentication in Azure AD
Passwordless authentication reduces the risk of phishing and password brute-force attacks. Users can authenticate up to 3 times faster. This means help desks should receive fewer password reset requests.
Passwordless authentication for Azure AD is now available globally. You can deploy three different passwordless authentication methods for your Azure AD users:
- Windows Hello for Business (Platform Authenticator, hardware)
- Security key login with FIDO2 security keys (Roaming Authenticator, hardware)
- Phone login with Microsoft Authenticator app (Roaming Authenticator, software)
Plan your passwordless deployment
At first, it may seem counterintuitive to tell users they’ll be able to log in to their computers and Microsoft 365 services without a password. Rest assured, the FIDO2 standard is resistant to the most common threats to authentication methods. To test the waters, you should include the use of USB tokens in proof-of-concept projects. This will help understand whether passwordless authentication is feasible. Sometimes, companies can’t use USB hardware, or USB ports must be disabled.
First, you’ll want to get an idea of what your deployment will look like for planning and scaling purposes. Fortunately, Microsoft includes the Passwordless Authentication Wizard in the Microsoft 365 admin center. This helps organizations determine which passwordless authentication methods best suit their needs:
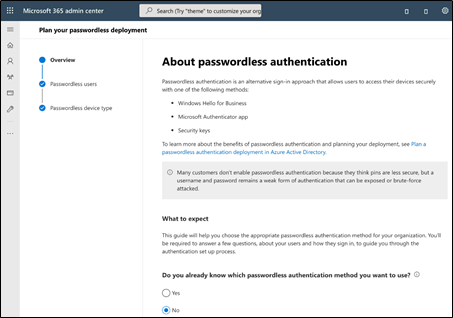
For example, if your users have PCs with biometric hardware, they can use Windows Hello for Business. This way, they can take advantage of single sign-on capabilities for their on-premises and cloud resources. The wizard covers all types of your identities, such as:
- frontline workers who have their own devices
- identities that share the same hardware at work.
You can choose the method that best suits your organizational needs. You will also receive recommendations on how to successfully launch this feature within your organization.
Enable passwordless authentication for Azure AD identities
You are now ready to begin the process for Azure AD identities. Azure AD can use all certified FIDO2 devices and enable passwordless authentication on all connected services and applications.
Note: FIDO2 is backward compatible with U2F. This means that, in general, a FIDO2 authentication device can also be used as a pure MFA device. Unfortunately, Microsoft does not offer this option in Azure. Furthermore, the Microsoft Authenticator app can perform both MFA and passwordless authentication.
When deploying passwordless authentication, you must first enable one or more pilot groups. You can enable FIDO2 for a single user or a group of users. Below is an example of how to enable FIDO2 for a single user:
*First, an administrator must enable the passwordless authentication option. This can be done for individual users, a group of users, or all users.
How to enable FIDO2 in Azure AD
- Log in to the Azure AD admin center.
- Navigate to Azure Active Directory > Security > Authentication methods > Authentication method policy.
- Under the FIDO2 Security Key method, choose the following options:
- Enable – Yes or No
- Target – All users or Select users
- Save the configuration.

Once your users are enabled, they can set up their FIDO2 device by going to https://myprofile.microsoft.com. Registering the FIDO2 device is simple, and the process is similar to setting up MFA. If the FIDO2 device has additional biometric security, that is also configured. If the device doesn’t have biometrics, a simple tap on the FIDO2 device proves human presence.
Note: Currently, there is no way to pre-provision FIDO2 security keys to users.
How to configure a FIDO2 device
- Navigate to https://myprofile.microsoft.com.
- Click on Security Info.
- If the user has already registered an Azure AD MFA method, they can immediately register a FIDO2 security key.
- If they don’t have at least one Azure AD MFA method registered, they need to add one.
- Add a FIDO2 security key by clicking Add Method and choosing Security Key.
- Choose USB device or NFC device.
- Prepare your key and choose Next.
- A box appears asking the user to create/enter a PIN for your security key. Then they must perform the required gesture for the key, either biometric or touch.
- The user is returned to the combined registration experience. They are then prompted to provide a meaningful name for the key to accurately identify it. Click Next.
- Click Done to complete the process.
Monitoring and auditing
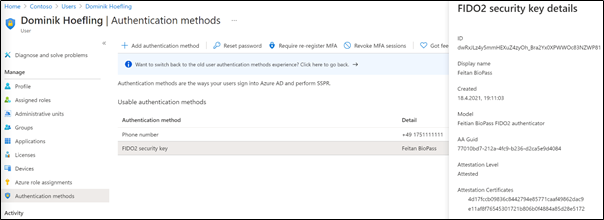
Now that your users have successfully completed the process, an administrator can review and control all of your users’ registered authentication methods in the Azure AD admin center:
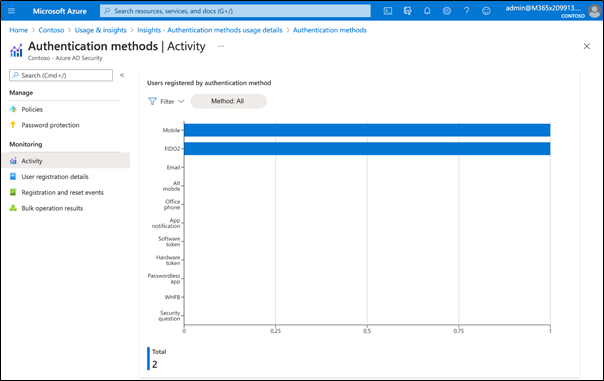
Azure AD includes reports that provide robust technical and business insights. You should monitor your pilot users to see if they encountered any issues during signup or authentication. You should also determine if sign-in is working properly. The preview version of the Authentication Methods Activity report provides you with a modern chart. You can get previews of all relevant reports. For example, the figure below shows the authentication method used in my tenant:
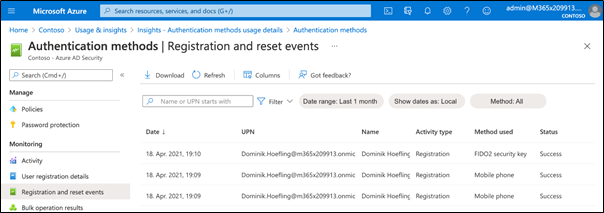
The registration and reset events will allow you to verify the registration process. They also allow you to see whether the registration of a FIDO2 security key was successful or not:
Manage Methods Using PowerShell
The Microsoft Graph PowerShell SDK includes cmdlets that allow administrators to manage user authentication methods. Currently, you can get and delete FIDO2 authentication methods for users:
Install-module Microsoft.Graph.Identity.Signins
Connect-MgGraph -Scopes UserAuthenticationMethod.ReadWrite.All
Select-MgProfile -Name beta
Get-MgUserAuthenticationFido2Method -UserId Dominik.Hoefling@m365x209913.onmicrosoft.com | fl
AaGuid : 77010bd7-212a-4fc9-b236-d2ca5e9d4084
AttestationCertificates : {4d17fccb09836c8442794e85771caaf49862dac9, e11af8f76545301721b806b0f4884a85d28e5172}
AttestationLevel : attested
CreatedDateTime : 4/18/2021 5:11:03 PM
CreationDateTime : 4/18/2021 5:11:03 PM
DisplayName : Feitan BioPass
Id : dwRxJLz4y5mmHEXuZ4zyOh_Bra2Yx0XPWWOc83NZWP81
Model : Feitian BioPass FIDO2 authenticator
AdditionalProperties : {}Additionally, you can also use Microsoft Graph to manage user authentication methods.
Handling Lost or Stolen FIDO2 Authenticators
Lost or stolen FIDO2 devices are generally protected against unauthorized use. Depending on the device, protection includes either:
- a 6-digit PIN code (required for Azure AD),
- a biometric function.
Additionally, this setting can be set individually for each Relying Party, so different providers may handle it differently. The device should be reported as lost or stolen as soon as possible so the administrator can remove it from Azure AD.
The W3C recommends registering a fallback authenticator for each service or application. This incurs additional costs and requires re-registration with the service. If many services are used, re-registration can be time-consuming. However, an extension to the WebAuth API describes a new prototype approach to account recovery. Essentially, the approach involves applying a key agreement scheme. This allows a primary and fallback authenticator to agree on a common EC key pair. Only the fallback authenticator can derive the private keys. And no additional registration with the fallback authenticator is required. The fallback authenticator must always be located in a secure location.
Overview: Temporary Pass
One of the most frequently asked questions about this is:
“How can organizations go truly passwordless and onboard new users?”
The Temporary Access Pass allows users to register a passwordless authentication method. They regain access to their account without a password by first authenticating with a temporary access code. Instead of giving your users a temporary password, the passcode serves as a temporary password:
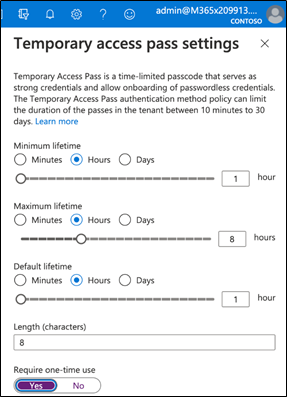
Once a user has a valid passcode, they can use it to log in and register a FIDO2 device from the “My Security Info” page. Or they can enroll for passwordless authentication from the Authenticator app.
Conclusion
Using passwords to authenticate to services is a common and established method for decades. Users tend to use simple, memorable passwords. They often borrow words from other people’s environments or use dictionaries. Brute-forcing passwords has little impact on password security. In fact, the most common cause of password theft is phishing.
The FIDO2 standard from the FIDO Alliance and the W3C is attractive for many reasons. The most important is that it significantly increases the security of service authentication. It also makes it as convenient as possible for users. The Authenticator’s automated key management eliminates the need for time-consuming administration, which can become costly for organizations. Furthermore, research has shown that the FIDO2 standard is resistant to the most common threats. That said, traditional authentication methods—primarily passwords—will likely remain in place for a long time.
