Azure Networking Fundamentals
What is a VNet?
A virtual network, or VNet, is an independent network within the Microsoft Azure cloud. Thus, a VNet in Azure offers a range of networking capabilities comparable to those of AWS’s Virtual Private Cloud (VPC). These features include:
- the DNS,
- routing,
- customization of DHCP blocks,
- access control,
- connectivity between virtual machines (VMs)
- virtual private networks (VPNs).
An Azure VNet is a representation of a network in the cloud. It therefore provides logical isolation of the Azure cloud for a subscription. Under the hood, it is a software abstraction of a network. This network sits on top of Azure’s infrastructure to provide isolation from resources outside the VNet. It is essentially a private network. However, the VNet can connect to other VNets in Azure. It can also connect to connected on-premises infrastructure to create hybrid systems. Operationally, a VNet follows common IP routing principles to connect resources within it. Therefore, it must be associated with one or more CIDR address spaces. So these can be segmented into subnets, within which resources will reside.
Using VNets
VNets can be used for:
- Create a dedicated private VNet, reserved for the cloud, to allow services and VMs in the VNet to communicate directly.
- Securely expand a data center by creating traditional site-to-site (S2S) VPNs. This allows for scalable capacity while maintaining excellent security.
- Then deploy hybrid clouds by securely connecting cloud-based applications to on-premises systems.
The components of VNets
The main components of Azure VNets are:
- Subnets : Divide a VNet into subnets. Or configure routing tables and network security groups (NSGs) for a subnet.
- IP Addresses : Assign public or private IP addresses to an Azure VNet.
- Use the public IP address for communications with the public. A dynamic IP will be assigned.
- Use the private IP address for connectivity within a VNet when using a VPN gateway or ExpressRoute. A dynamic IP address is assigned by default, but a static IP address can also be assigned.
- Network Security Groups (NSG) : Allows you to allow or deny traffic to a subnet or network interface.
- Firewall : A firewall service allows granular control of network input/output.
- Load Balancing : The three load balancing solutions offered by Azure are:
- Azure Traffic Manager – comparable to Route53 in AWS
- Azure Load Balancer
- Azure Application Gateway
- Routing tables : When traffic leaves a subnet, routing is required to forward packets to other networks. A router uses a routing table for custom configuration. The routing table can contain rules that define where traffic should go:
- a virtual network,
- a virtual network gateway
- a virtual machine.
- A user-defined route, or UDR, can be used to forward traffic to a different VNet. It’s worth noting that this is a powerful tool for establishing a connection between hubs.
Azure VNet Overview
Resources in Azure always require some form of networking solution to communicate with other resources. Therefore, it is necessary to have a logical construct to which the resources are linked. Since everything runs over a network, a virtual network space in the cloud is typically used. For Azure, this is called the Azure Virtual Network, or VNet. It allows many types of Azure resources to reside in a VNet, such as Azure Virtual Machines (VMs). One or more subnets can compose a VNet. It can then allow them to securely communicate with each other, the internet, and on-premises networks. The scope of a virtual network is a single region; however, multiple virtual networks from different regions can connect to each other through virtual network peering, as illustrated below:
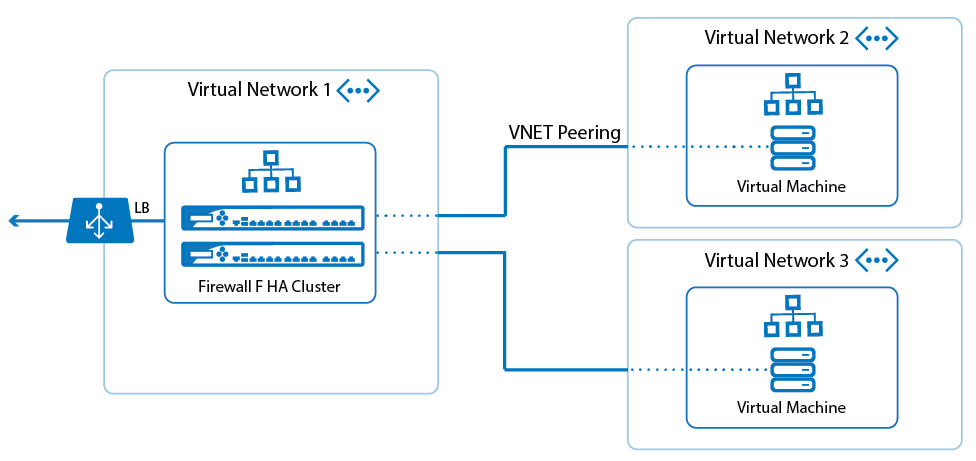
Azure Virtual Network offers the following important features:
- Specify a private IP address space using public and private addresses (RFC 1918). Azure assigns a private IP address to resources in a virtual network from the address space you assign.
- Segment the virtual network into one or more subnets. Then, allocate a portion of the virtual network’s address space to each subnet.
- Use the name resolution provided by Azure. Or specify your own DNS server used by resources connected to a virtual network.
Security and traffic control policy
You can filter network traffic between subnets using one or both of the following options:
- Network Security Groups (NSGs): Network security groups are a container for the rule set. The rule set contains one or more rule sets that dictate what type of traffic can pass through. Each individual rule can have a source, destination, protocol, and action. The source and destination can be an IP address, a VNet, or an Application Security Group.
- Application Security Group (ASG): ASGs define the source/destination with a label instead of the IP. An ASG is an arbitrary definition that can be applied to resources, such as “AppServer”, “DataBase”, “myApp”, etc. This definition can then be used in a rule inside an NSG. This is useful when a rule needs to apply to resources based on their purpose. This provides greater flexibility in policy enforcement.
- Azure Managed Firewall: Azure provides a managed firewall that controls traffic between the VNet and the internet. Specifically, this firewall is designed to protect internet-facing conversations. Note that this firewall requires its own subnet. It then routes traffic to other resources using internal routing.
- Virtual Network Appliance: For third-party integration, a virtual network appliance can be inserted into a VNet. Essentially, this appliance is a virtual machine that runs a network function, such as a firewall.
VPN with VNet
It is common to need to connect cloud resources to on-premises resources. This normally requires setting up a virtual private network (VPN) between the two environments. As mentioned earlier, Azure VNet also supports VPN connectivity. Therefore such connectivity can be established between different VNets, or from one VNet to on-premises as shown in the image below.
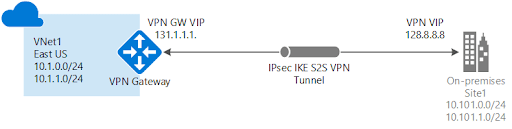
Azure supports different VPN modes, such as Site-to-Site, Point-to-Site, Policy-based, and Route-based. So this gives the user the flexibility to choose the best option for their tunnel based on their needs. A few key components go into the configuration:
- Virtual Network Gateway : The virtual network gateway sits at the edge of a VNet’s subnet. It enables connectivity between that subnet and other networks or VPNs. This is where most of the VPN configuration is located.
- Local Network Gateway : The Local Network Gateway is a representation of the clients’ gateway. Also, it simply contains the configuration that the tunnel needs to know to build a VPN tunnel to the other end.
- Border Gateway Protocol (BGP) : In a hybrid cloud, both endpoints must know each other at the network level. To efficiently learn on-premises routes, a routing protocol is required. BGP is the current choice, and Azure supports BGP over IPSec. By running BGP, you can propagate local BGP routes to your cloud and on-premises routers without intervention.
